🚨 The $4.7 Million AWS Root Account Mistake
In March 2024, a mid-sized fintech company discovered unauthorized cryptocurrency mining operations running across 847 EC2 instances in their AWS account. The breach lasted 73 days undetected, resulting in:
in total damages including AWS charges, investigation costs, regulatory fines, and business disruption.
The root cause? Their AWS root account had no MFA protection and was being used for daily operations by multiple team members.
🎯 Want Our Complete AWS Security Checklist?
Don't secure just your root account—get our comprehensive 20-point security checklist that covers all critical AWS configurations. Used by 500+ companies to prevent security incidents.
📋 What You'll Learn
🎯 Why AWS Root Account Security is Critical
Your AWS root account is like the master key to your entire cloud infrastructure. Unlike other user accounts, the root account has unrestricted access to every service and resource in your AWS account—including the ability to:
- Close your AWS account permanently
- Change billing information and payment methods
- Create, modify, or delete any AWS resource
- View and download detailed billing reports
- Enable or disable AWS services
- Modify support plans and contact preferences
The Three Most Common Root Account Vulnerabilities
Without MFA, your root account is protected only by a password. If this password is compromised through phishing, data breaches, or brute force attacks, attackers gain complete control of your AWS environment.
Many teams use the root account for routine tasks, increasing exposure risk. Each login creates an opportunity for credential theft, and shared root credentials among team members amplify this risk exponentially.
Root account access keys stored in code repositories, configuration files, or CI/CD systems represent the highest-risk scenario. These credentials, if discovered, provide unrestricted API access to your entire AWS account.
Prerequisites:
- Access to your AWS root account credentials
- A smartphone with authenticator app (Google Authenticator, Authy, or Microsoft Authenticator)
- Alternative: Hardware MFA device (recommended for production environments)
Console Steps:
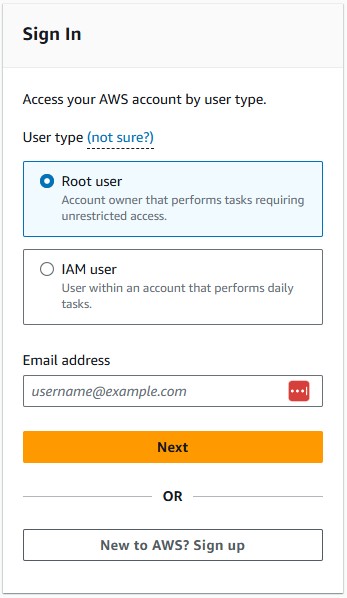
1.1 Sign in to AWS Console
- Go to
https://console.aws.amazon.com/ - Select "Root user" and enter your root account email
- Enter your root account password
📸 Screenshot: AWS Console sign-in page with "Root user" selected
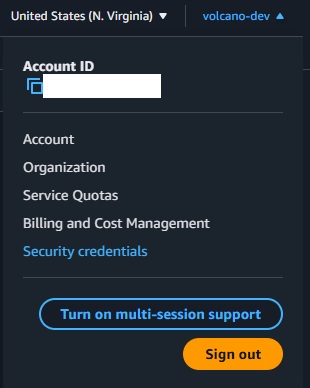
1.2 Navigate to Security Credentials
- Click on your account name in the top-right corner
- Select "Security credentials" from the dropdown menu
📸 Screenshot: Account dropdown menu with "Security credentials" highlighted
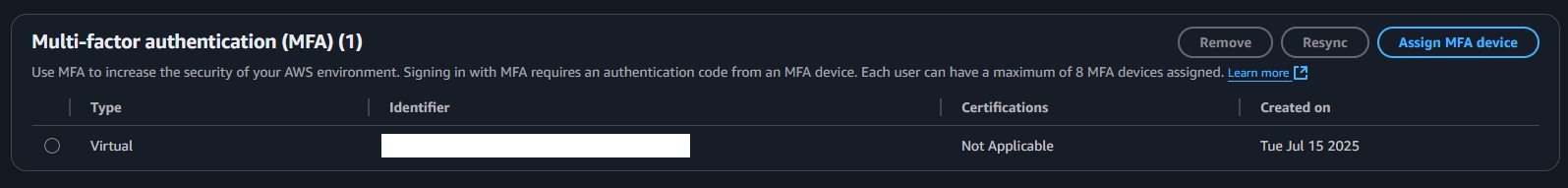
1.3 Enable MFA
- Find the "Multi-factor authentication (MFA)" section
- Click "Activate MFA"
- Choose "Authenticator app" (recommended for most users)
- Click "Continue"
📸 Screenshot: MFA setup wizard showing authenticator app option
1.4 Configure Your Authenticator App
- Open your authenticator app on your smartphone
- Scan the QR code displayed in the AWS Console
- Enter the first 6-digit code from your app
- Wait for the code to refresh, then enter the second code
- Click "Add MFA"
Instead of using the root account for daily operations, create IAM users with administrative privileges. This follows the principle of least privilege while maintaining necessary access.
Console Steps:
2.1 Navigate to IAM Service
- In the AWS Console, search for "IAM" in the services search bar
- Click on "IAM" to open the Identity and Access Management console
2.2 Create Admin User Group
- Click "User groups" in the left navigation panel
- Click "Create group"
- Group name:
Administrators - Attach policies: Search and select
AdministratorAccess - Click "Create group"
2.3 Create IAM Administrative User
- Click "Users" in the left navigation panel
- Click "Create user"
- Username:
admin-[your-name](e.g., admin-john-doe) - Check "Provide user access to the AWS Management Console"
- Select "I want to create an IAM user"
- Choose "Custom password" and create a strong password
- Uncheck "Users must create a new password at next sign-in"
- Click "Next"
2.4 Add User to Admin Group
- Select "Add user to group"
- Check the "Administrators" group you created
- Click "Next"
- Review the configuration and click "Create user"
2.5 Enable MFA for Admin User
- Click on the newly created user
- Go to the "Security credentials" tab
- In the "Multi-factor authentication (MFA)" section, click "Assign MFA device"
- Follow the same MFA setup process as for the root account
Root account access keys provide programmatic access to your entire AWS account without MFA protection. These should never exist for the root account.
Console Steps:
3.1 Check for Existing Access Keys
- While signed in as root, go to "Security credentials"
- Scroll down to the "Access keys for CLI, SDK, & API access" section
- Check if any access keys are listed
3.2 Delete Any Existing Access Keys
- For each access key listed:
- Click "Actions" → "Delete"
- Type "Delete" to confirm
- Click "Delete"
3.3 Verify No Access Keys Remain
- Refresh the Security credentials page
- Confirm the "Access keys" section shows "No access keys"
Monitor root account usage to detect unauthorized access attempts or accidental usage by team members.
Console Steps:
4.1 Create CloudWatch Alarm for Root Account Usage
- Navigate to CloudWatch service
- Click "Alarms" in the left panel
- Click "Create alarm"
- Click "Select metric"
- Choose "CloudWatchLogs" → "Metric Filters"
- Create a new metric filter for root account usage
4.2 Configure Root Usage Metric Filter
4.3 Set Up Email Notifications
- Create an SNS topic:
root-account-usage-alerts - Subscribe your security team's email to this topic
- Configure the CloudWatch alarm to send notifications to this SNS topic
4.4 Enable CloudTrail (if not already enabled)
- Navigate to CloudTrail service
- Click "Create trail"
- Trail name:
security-audit-trail - Enable "Log file validation"
- Choose an S3 bucket for log storage
- Enable CloudWatch Logs integration
- Click "Create trail"
🔍 Validation: Verify Your Root Account Security
Complete these checks to ensure your root account is properly secured:
- MFA Test: Sign out and sign back in. You should be prompted for both password and MFA code.
- Access Keys Check: Verify "No access keys" appears in Security credentials.
- IAM Admin Test: Sign in with your new IAM admin user and verify you can perform administrative tasks.
- Monitoring Test: Trigger a root login and confirm you receive an alert email within 5 minutes.
- CloudTrail Verification: Check CloudTrail logs to ensure root account activities are being recorded.
Security Validation Script
Run this script to programmatically verify your root account security:
🔧 Advanced Root Account Security (Optional)
Hardware MFA for Production Environments
For production AWS accounts handling sensitive data, consider upgrading to hardware MFA devices:
- YubiKey 5 Series: USB/NFC hardware authenticator ($45-70)
- Gemalto SafeNet: Professional-grade hardware token ($50-100)
- AWS Support Recommended: Thales/Gemalto devices for enterprise use
Root Account Contact Information
Ensure AWS can contact you about security issues:
- Go to Account Settings → Contact Information
- Verify all contact details are current
- Add alternate contacts for security notifications
- Enable security contact preferences
Billing Alerts for Unauthorized Usage
Set up billing alerts to detect unauthorized resource usage:
❌ Common Root Account Security Mistakes to Avoid
🚀 Next Steps: Complete AWS Security
Securing your root account is just the first step. Here's what to tackle next:
AWS Config tracks configuration changes and compliance with security best practices across all your AWS resources.
Secure your S3 buckets against public access and data breaches—the #1 cause of AWS security incidents.
Enable intelligent threat detection to identify malicious activity and potential security threats automatically.
Configure VPCs, security groups, and NACLs to create defense-in-depth network security.
🎯 Ready to Secure Your Entire AWS Environment?
Root account security is critical, but it's just one piece of the puzzle. Get our complete AWS security assessment to identify all vulnerabilities in your environment.